AI Office

Ever miss the start of a big game because your streaming app froze? Or spent ages searching for a movie only to find it’s not there? Streaming should be fun, not frustrating. IYFTV is a platform that promises easy access to shows, movies, and live events. It’s built for people who want entertainment without the fuss. This guide provides an overview of everything related to IYFTV. It covers what it is, how to set it up, and how to fix common hiccups. Let’s see why IYFTV could be the answer to better streaming.
Recent blog posts

How to Use IYFTV to Stream Your Favorite Shows Easily
2025-06-10 10:08:17

How to Clear Teams Cache to Fix Issues Fast
2025-06-10 07:11:41

18dsg7 Python Explained: Features, Use Cases, and Benefits
2025-06-09 06:01:17

MyLawyer360: Your Complete Guide to Modern Legal Support
2025-06-07 05:58:33
All blog posts
Posted On Saturday, 8 Mar 2025

AMD Radeon Software: Key Features, History, and Future Outlook
Radeon Software by AMD is an essential tool for Radeon graphics card and APU users by delivering robust functions that improve both system efficiency and gaming quality and optimize overall performance. The software system began life as a catalyst and has transformed through time to include gaming optimization and performance monitoring and recording functionalities. In this article, we will discuss the history, key features, recent developments, and future outlook of Radeon Software, highlighting its impact on the graphics world.
Posted On Friday, 7 Mar 2025
What Is a Personal Area Network (PAN): Features & Benefits
A personal area network or pan covers a small area, it usually covers a 10-meter radius. It's smaller than other networks like MAN, LAN or WAN. It helps in sharing of data and access to resources with ease, offering a convenient and efficient means of connecting personal devices.
Posted On Thursday, 6 Mar 2025

What Is Scada Software In Cybersecurity?
SCADA systems are used in industrial processes to monitor real-time data. SCADA (Supervisory Control and Data Acquisition) is utilized across multiple sectors, such as energy, water treatment, and manufacturing. It integrates hardware and software to manage real-time data and automation tasks. The role of cybersecurity in SCADA is crucial because these systems are connected to computers and private networks, and any system connected to the internet is always at risk of cyber attacks, such as hacking, malware, or unauthorized access. Protecting SCADA from these threats is essential to prevent damage to critical infrastructure.
Posted On Thursday, 6 Mar 2025

What is the POD 4 Ultra? Features, Price, and Review
Have you ever desired better sleep than what you obtain from night-time temperature adjustments through uncomfortable devices? The Eight Sleep Pod 4 Ultra is the best solution for your improved sleep needs. Such an innovative mattress cover employs advanced technological capabilities to generate tailored sleep conditions while collecting valuable sleep data through advanced tools which do not require wearable devices.In this article, we’ll explain what the POD 4 Ultra is, how it works, its main features and if it's worth the price. Keep reading to learn how it can make you sleep better.
Posted On Wednesday, 5 Mar 2025

Digital Tech Time: Strategies for Effective Technology Management
“Digital tech time refers to the time spent on computers, the internet, and other digital devices, such as playing games, reading online books, and other online activities.” In today's world, we heavily rely on these digital activities, like studying online, shopping, and managing our banks online, and there's almost nothing we can't do online. So, we've seen digital tech time increase over time. Let's check how it increased, especially during the pandemic, from the start until 2025. Then, we'll discuss how we can manage technologies with effective strategies.
Posted On Wednesday, 5 Mar 2025
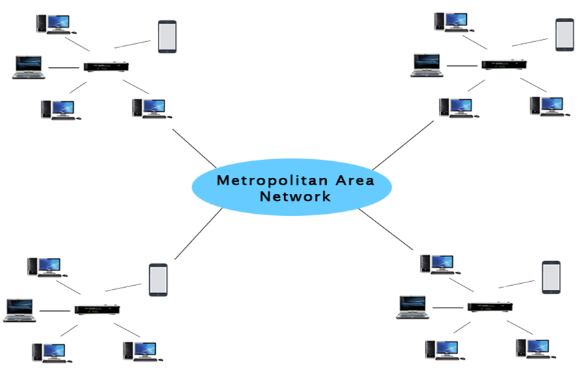
Metropolitan Area Network: Working, Advantages & Disadvantages
A Metropolitan Area Network (MAN) connects multiple computers in a specific geographical area. It is larger than a Local Area Network (LAN) and smaller than a Wide Area Network (WAN). With MAN technology providing high-speed internet access to all citizens, traffic flow is optimized and public services are better coordinated than ever before. This potent network solution enables cities to experience greater connectivity and quality of life, with everyone having fast online access whenever needed.
Posted On Tuesday, 4 Mar 2025

Why Pesudocode Is Important In Programming Language
Whenever we work on a new idea, we need to do two basic things: test it and design it. Pseudocode helps us with these tasks. It focuses on the logic of the idea, so a programmer doesn't need to worry about the specific rules of the programming language. It guarantees that our program will function as planned and facilitates communication with others. Persuadocode tells us how a program and an algorithm work. It doesn't use complex programming language; it uses simple everyday language, like English, which tells us to solve different problems easily.
Posted On Monday, 3 Mar 2025

What Is a Network Security Key? Easy Method To Find It
A network security key, commonly referred to as a Wi-Fi password, is the key used to access a wireless network. It prevents people who are not authorized from accessing the network, protecting data from unauthorized access. With technology advancing at such a fast pace, it has become more important than ever to know and control your network security keys. An in-depth analysis of network security keys, provides current data and new perspectives to help you better understand the complexities.
Posted On Monday, 3 Mar 2025

Jira Work Management
Today, everything is being done remotely; even employees are discussing and submitting their projects online. Some tools help manage projects, and Jira Work Management plays a similar role. However, do you know what is Jira work management is? JWM is not like other project management tools. Project management tools come in various types, and traditional project management tools primarily focus on deadlines and task assignments. However, modern tools like Jira handle work management automation, real-time responses, and seamless team collaboration simultaneously. Its interface is so easy and flexible that even non-technical people can use it. In 2025, its usage is increasing significantly, so what makes it stand out from its competition? The most important question is how teams manage tasks and perform different actions within it.
Posted On Saturday, 1 Mar 2025
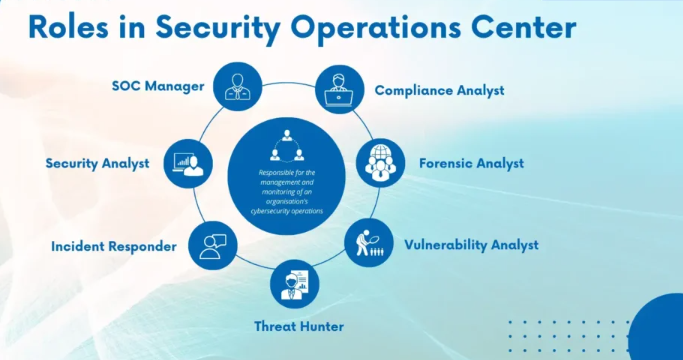
How to Become a Security Operations Center Analyst: Skills Needed & Scope
At this time, the trend of cybersecurity is at the top because everything is being converted to digital work. Companies' important data is stored on cloud-based servers. Therefore, the demand for Security Operations Center Analysts is also increasing. “A Security Operations Center analyst detects threats, then analyzes them, and also responds to them.” In this way, they play an important role in keeping the system's data safe. Since the data of large companies is important, they invest a significant amount in cybersecurity, and therefore they need a SOC. This is the reason why the value and scope of this degree are increasing. But what will be its scope in 2025 and its value in the future, and what skills are required to become a SOC? This article will try to cover every aspect of this degree.
Posted On Saturday, 1 Mar 2025

What Is Ping
Most articles inform you that Ping is merely a utility to test response time on the network. But did you ever wonder why Ping exists in the first place? Ping is not merely a test of the internet—it's an actual live check that assesses how smoothly the whole online universe operates. Let's discuss in detail how Ping works and everything you need to know about it because Ping is more than just a network command.
Posted On Friday, 28 Feb 2025
How to Implement Stochastic Gradient Descent In R
SGD Stochastic Gradient Descent helps the machines to work faster. It offers a more straightforward algorithm to train the machines more quickly. It help in determining a model's optimal settings by gradually making minor changes. “Stochastic Gradient Descent (SGD) is used because it is highly efficient for training machine learning models on large datasets. It updates model parameters using a single data point or a small random sample per iteration. It makes computation faster and using less memory compared to standard gradient descent methods that process the entire dataset at once.”
Recent blog posts
Migrating to AI 101
Sunday, 1 jan 2023

Migrating to AI 101
Sunday, 1 jan 2023

Migrating to AI 101
Sunday, 1 jan 2023

Migrating to AI 101
Sunday, 1 jan 2023